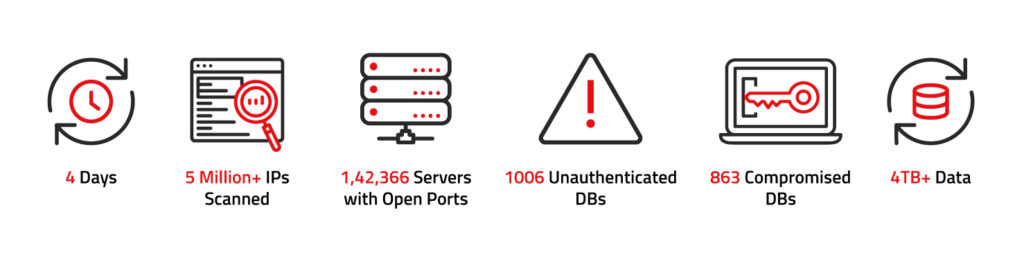
We scanned 5 million+ IP Addresses for database vulnerabilities : Analysis and Insights, 2020

Recently, in the month of August 2020, our team at TIKAJ conducted an extensive research to discover open Mongodb instances all over the internet. Even after 8 years of being reported Mongodb open port vulnerabilities are being exploited in wild for data breaches. With this research, we wanted to find out how educated and serious developers are about this vulnerability.
The Statistics
We scanned 5 million+ IP addresses over the internet within 4 days, out of which exactly 1,42,366 servers had port 27017 open for connection. What we discovered as a result of this 4 days long research, was a whopping number of 1006 unauthenticated Mongodb server instances, either compromised or waiting to be compromised.
Since the numbers amused us pretty well, we jumped in to get our hands dirty and reveal some more patterns in this vast data pool. Not to our surprise, out of these open unauthenticated database servers, 863 have already been compromised and breached, and are held for ransom. The total accumulative size of the discovered data is about ~ 4 Terabytes.
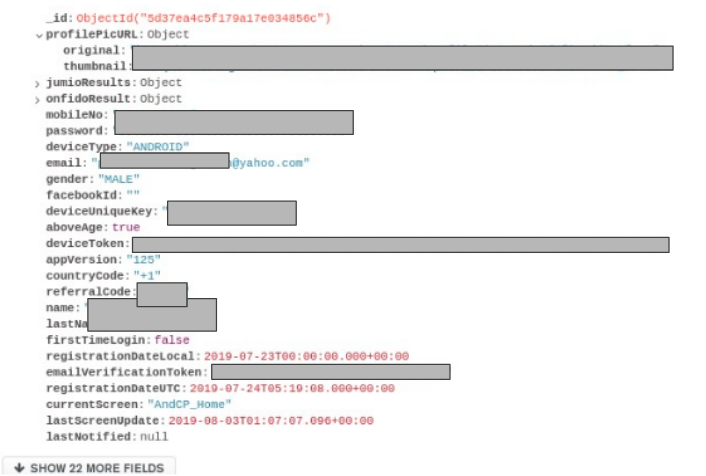
The discovered databases on servers include several datasets which have extensive personal information of individuals like phone number, email addresses, address, login information.
One such databases, that caught our attention is a known Canadian Massage Service Provider Company, that has its customer’s name, phone numbers, addresses, preferences, booking history and transactions database open in the internet. Moreover there are similar personal information of therapists and admins exposed via same database.
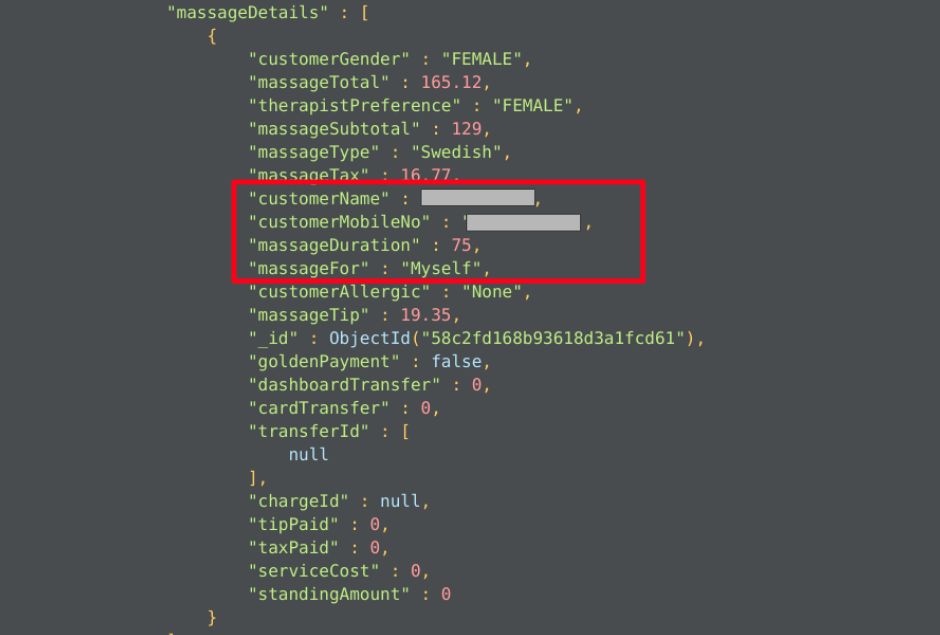
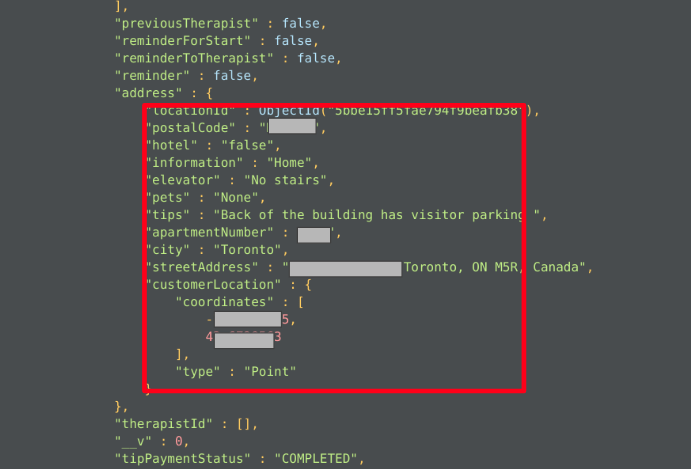
More interestingly they have even pinpointed the customer addresses precisely with Geo-coordinates and other suggestive landmarks, no doubt along with the exact postal address.
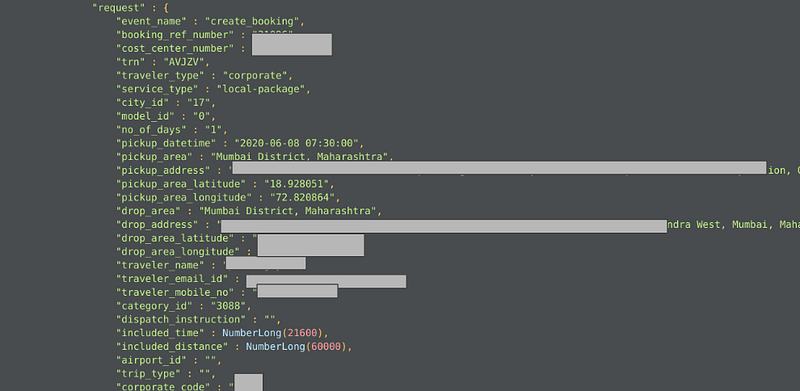
In another database, an Indian Corporate Cab Service Provider, has data exposed of their travelers along with their email address, phone numbers and pickup and drop coordinates.
Few more interesting datasets:
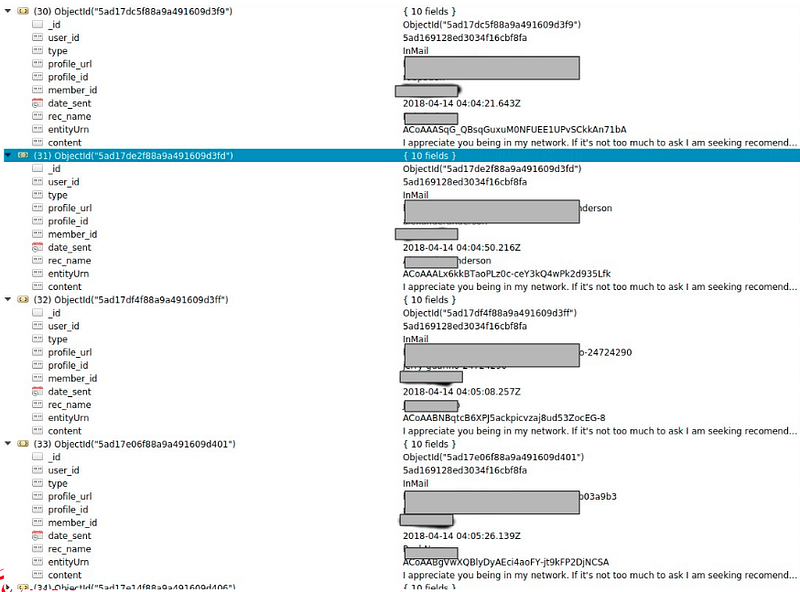
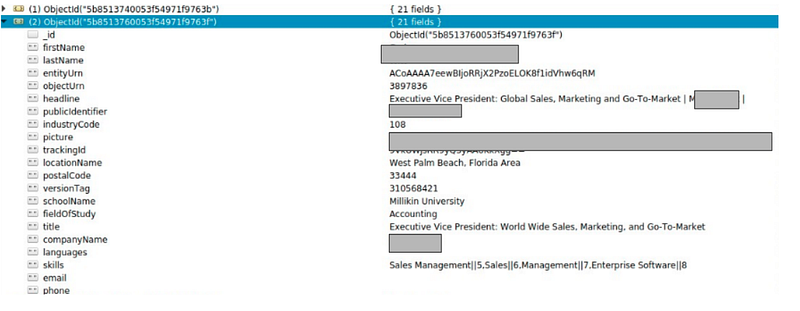
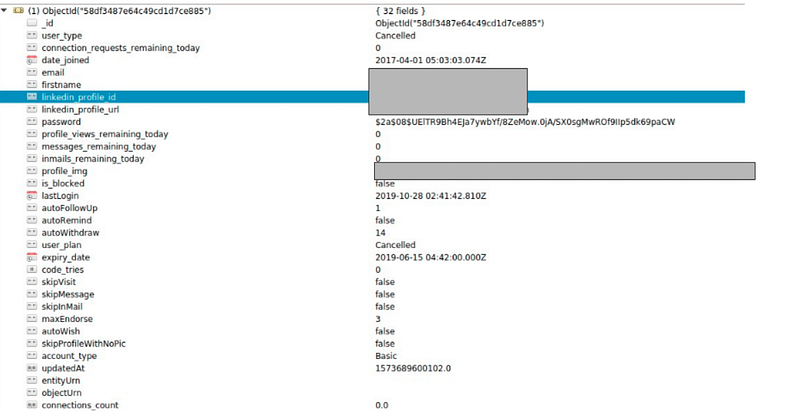
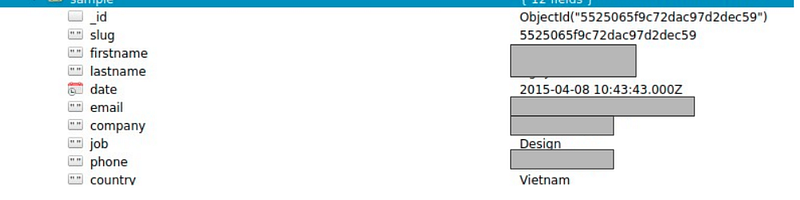
The affected industry types, as we have analysed, are Personal care services, Restaurant POS, E-commerce, Transaction based systems, Transport services, Educational Institutes and many more.
One can easily imagine, what cyber attacks can be pulled off with such variety of personal information of individuals — ranging from targeted social engineered phishing attacks to direct financial attacks.
There were several server credentials exposed through various configs stored in these vulnerable databases, which can be directly exploited for complete server compromises and data breaches.
Ransom Tale
The most interesting fact is that out of the discovered 1006 databases, 843 have already been compromised (i.e ~84%), held for ransom demands, and have still been unnoticed by the server owners! The attackers (being creative!) put up interesting HOW TO or README guides in collections to notify the owner of the databases that their databases have been backed up and that they must pay ransom in Bitcoins to avoid data leakage. One such pretty message is below.
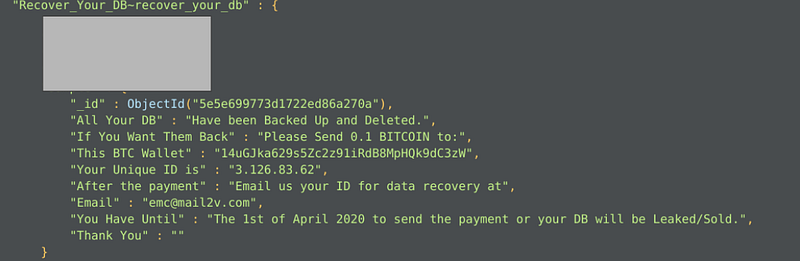
Interestingly, many attackers have coupled their ransom demands with the threat of filing complaints against DB owners under General Data Protection Regulation. One such message:
All your data is a backed up. You must pay 0.015 BTC to xxxxxxxxxxxxxxxxxxxxxx 48 hours for recover it. After 48 hours expiration we will leaked and exposed all your data. In case of refusal to pay, we will contact the General Data Protection Regulation, GDPR and notify them that you store user data in an open form and is not safe. Under the rules of the law, you face a heavy fine or arrest and your base dump will be dropped from our server! You can buy bitcoin here, does not take much time to buy https://localbitcoins.com with this guide https://localbitcoins.com/guides/how-to-buy-bitcoins
Top 5 Common database names
- admin
- config
- test
- local
- development
Top 5 Common collection names
- System.version
- System.sessions
- System.indexes
- Users
- User
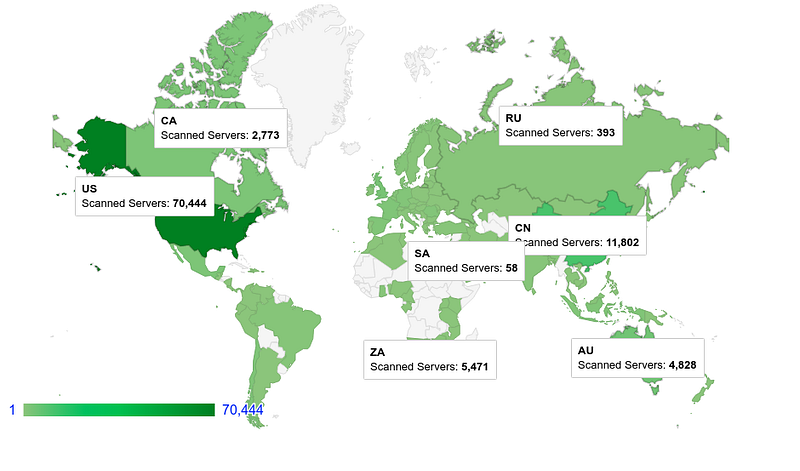
Geographical Distribution
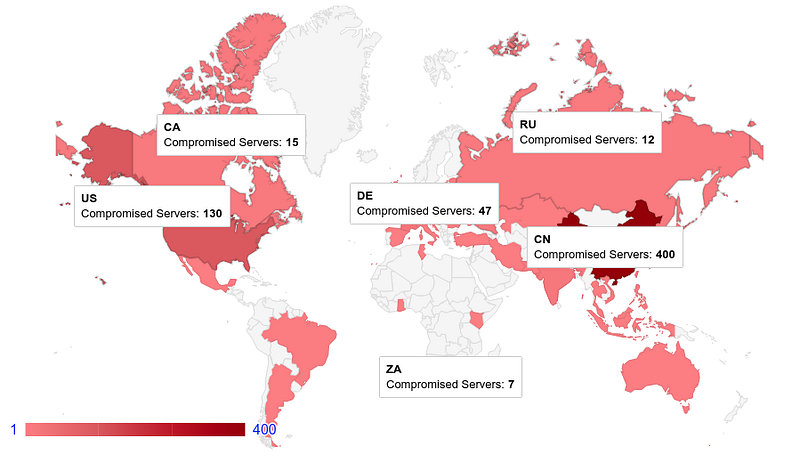
Geographically, the top distribution of discovered compromised servers countries has been as below.
- China : 400
- USA : 130
- Denmark : 47
- India : 25
- Singapore: 24
Below is a graphical distribution of the Servers with open ports and Compromised servers across Geo-locations.
We have discovered several other patterns which reveal interesting insights, summarizing which, we will be publishing a detailed research report soon. Our research, has concluded the fact that despite the increasing cyber attacks, server compromises and data breaches, there is a visible lack of awareness regarding the secure configuration practices among the developers. Organization’s handling sensitive user information have the responsibility of protecting them under various regulations — and ethically as well. But lack of expertise, human errors and mis-configurations are leading to large data breaches with inevitable financial and informational losses.
Gap in the system lies in the lack of secure development and deployment practices. Developers need to be educated about secure development practices, because Information Security is not just the work of the InfoSec team
To cope up with these problems, the organizations must adopt DevSecOps practices and regular penetration testings, compromise assessments and configuration reviews, identifying vulnerable server configurations and other vulnerabilities — and fixing them in speed.
Security is achieved with practice, not just by enforcement.
PS: We are in contact with some of the exposed server’s owner companies to enable authentication on the servers and harden their server configurations.
Act Now to patch up the security gaps in your infrastructure.
Get a free preliminary penetration test analysis of your infrastructure to get insights about your organization’s risk posture.






